Today I Learned
Microblogs of some small things I've learned.
Using dynamic DNS for home servers
It is often joked about sharing localhost URL with others, but there are scenarios where exposing a local port to the internet is genuinely useful. For instance, I can run a Plex media server at home instead of paying for Google photos, also stream my downloaded movies/shows from any device. Many internet providers use CGNAT for IPv4, which combined with NAT in home routers creates a double NAT. While this is cheaper for ISPs and also beneficial for security, it complicates exposing your home servers to internet.
With the advent of IPv6, things are changing. ISPs are now providing public IPv6 addresses. Since IPv6 addresses are plenty, NAT is typically not used. The remaining challenge is that IPv6 addresses are typically dynamic and change frequently. This is where dynamic DNS comes into play. By obtaining a domain name and running a dynamic DNS software, you can keep the DNS record updated whenever your home IPv6 address changes. This allows you to access your home servers using a static domain name instead of the ever-changing IP address.
Exposing home servers to internet can heavily undermine security of your home network. Not recommended unless you know what you are doing.
Here is my setup of Plex media server with dynamic DNS https://gist.github.com/ramenhost/9d26175abcbebf5c739e8de7d3ec3d13
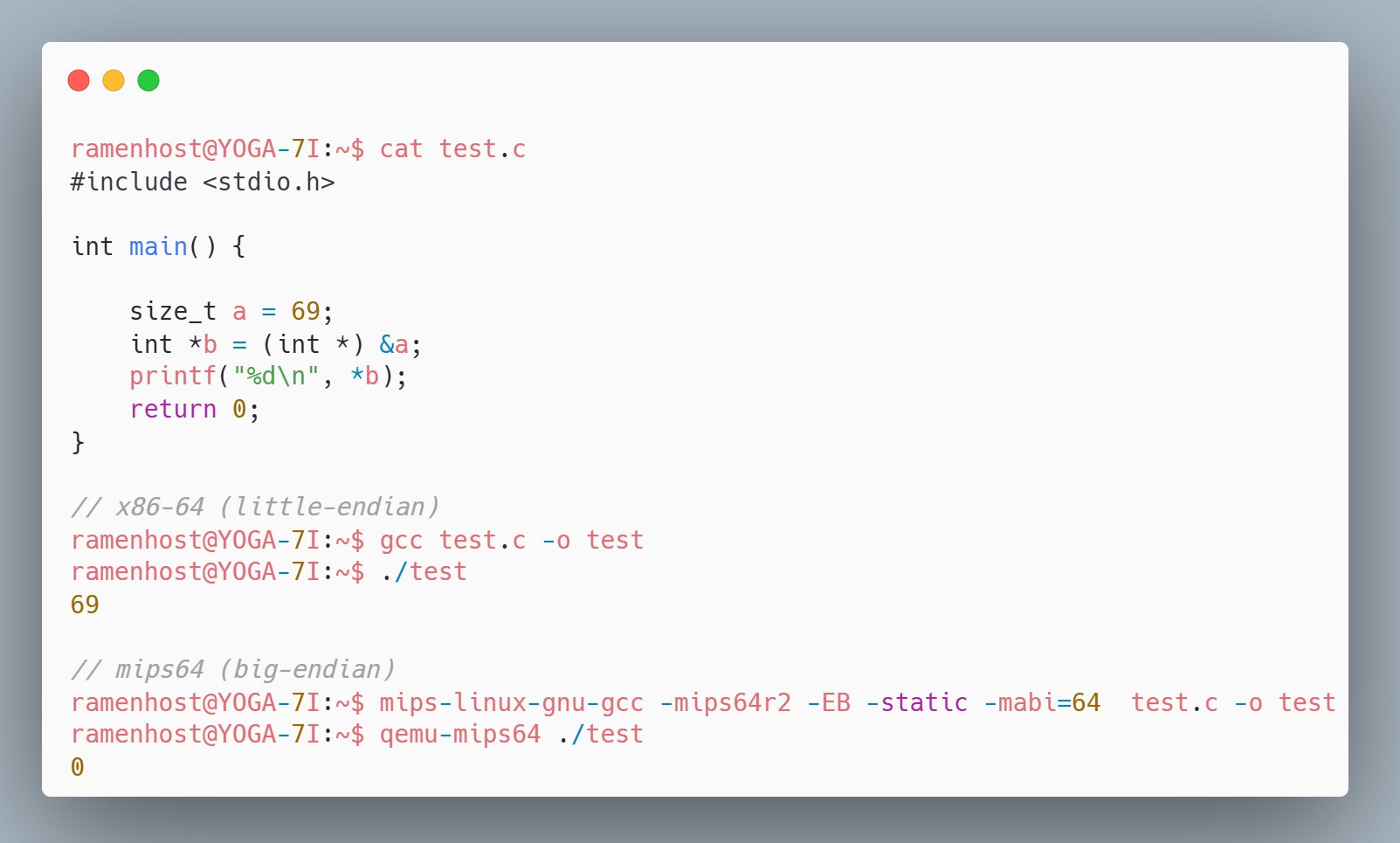
Typecasting pointers in C is arch-dependent
For years, I’ve been confidently downcasting pointers after checking for value overflow. Today I learned that typecasting pointers to a smaller datatype works only on little-endian architectures. On big-endian systems, the pointer will reference the most significant bytes, leading to unexpected results. I realized this the hard way when this PR failed CI with flying colors.
Cloudflare knows what http library you use
In X, @zoriya_dev shared an issue where an API request was blocked by Cloudflare when using Python’s aiohttp library, while the same request worked fine when using curl or the requests library. People got together in replies to investigate the issue.
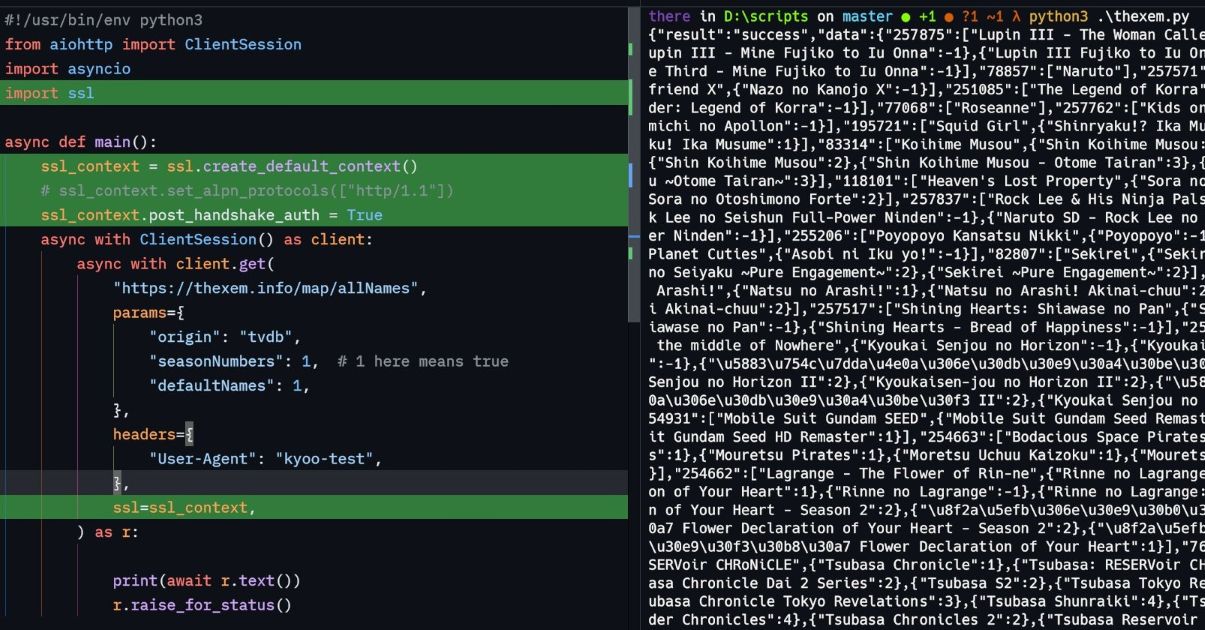
here is the python code (that gets cloudflare blocked)
— Zoe Roux (@zoriya_dev) September 20, 2024
the curl requests (that works)
and the netcat to print requests (by changing https://thexem by http://localhost), first is python second is curl https://t.co/eJZydIRbkK pic.twitter.com/8TSDb7WjMs
Initial analysis suggested that Cloudflare was blocking requests based on the User-Agent header. However, this theory was quickly disproven as the User-Agent header was identical in both aiohttp and curl requests. Even after ensuring that the entire HTTP request was the same for both libraries, the issue persisted. This indicated that the detection mechanism was operating at a lower level, likely involving TLS records.
Using Wireshark, I discovered that the TLS extensions differed between aiohttp and curl. By adding any single TLS extension to aiohttp, the block was bypassed, effectively disrupting the blacklisted fingerprint.
TLS fingerprinting is a common technique used by Cloudflare and other services to detect bots and malicious traffic. Cloudflare offers varying degrees of protection that can be configured by the domain owner. In this case, it is possible that the domain was put in a higher protection level where TLS fingerprint of aiohttp is blacklisted.